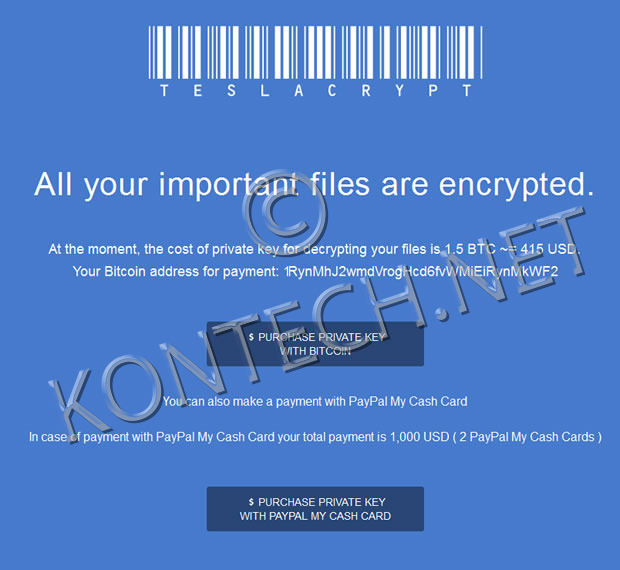
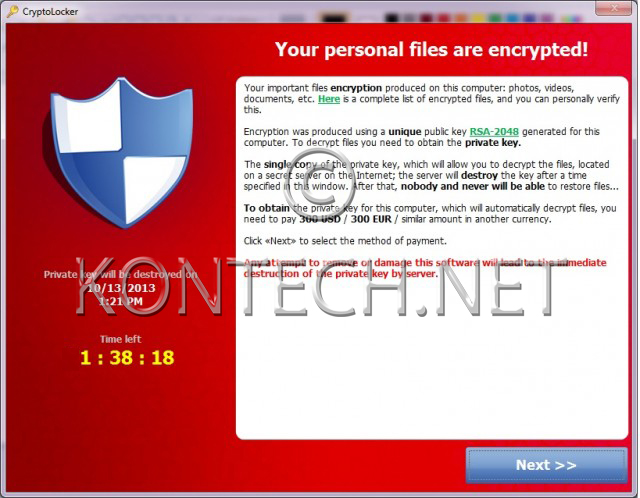
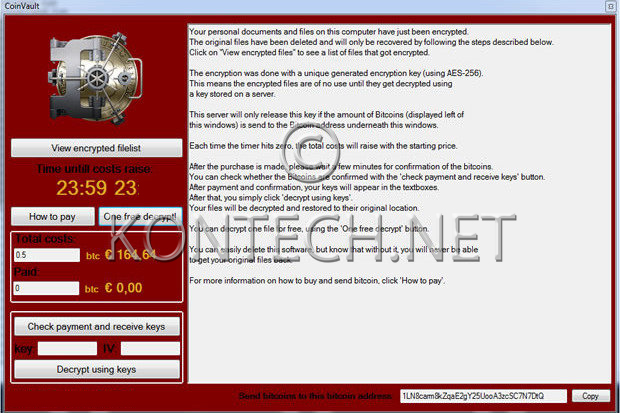
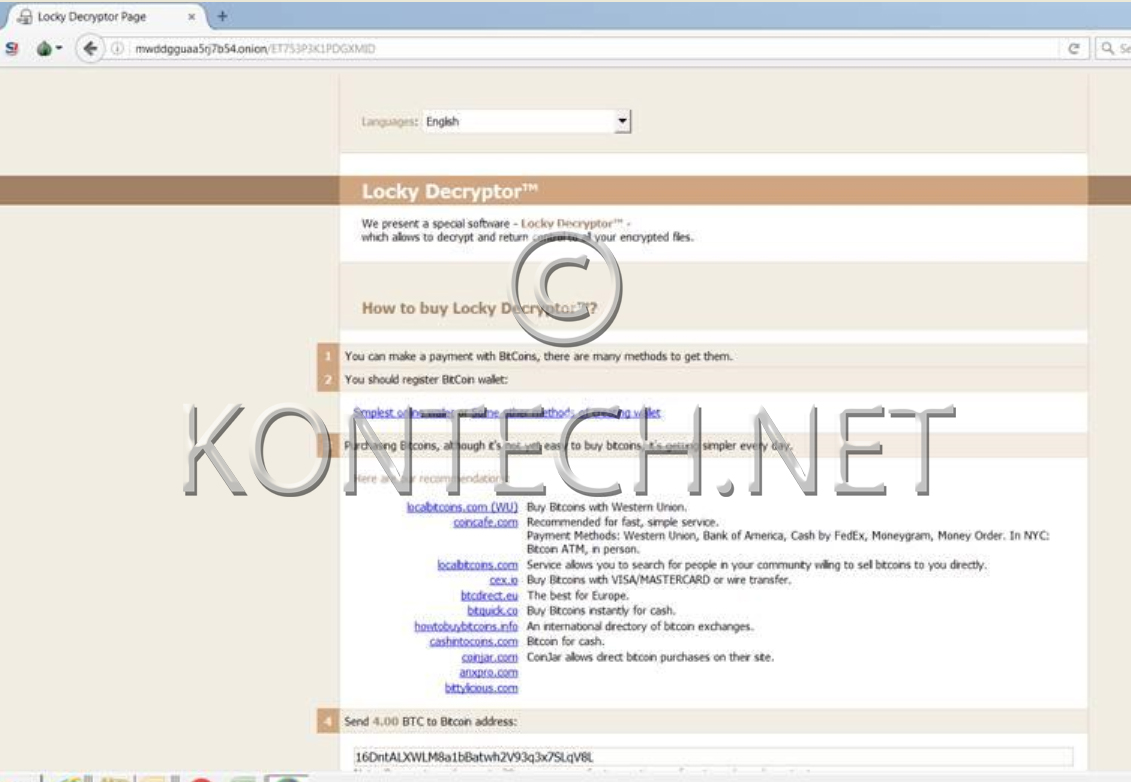
Pay the ransom infections to get data back or fight it and report it?
Unfortunately, once you’ve contracted ransomware your files and/or system are likely encrypted and your options are:
- Pay up the ransom in bitcoin and hope for the positive outcome
- Suck it up and cut your losses or “close the doors”
- Clean up your system(s) and restore from backup (if one exists and it’s working)
There seem to be different school of thought when it comes to dealing with ransomware attacks and infections. It all depends who you ask and what the specific circumstances are. If you talk to security gurus who deal with large and sophisticated networks, utilizing military-grade encryption, the typical answer you’re likely to get is: “Never pay the ransom!”
Even FBI seems to have different stance on the issue. Back in 2015, at Cyber Security Summit 2015, FBI Boston’s Joseph Bonavolonta said that: “paying the ransom is often the easiest path out of ransomware infections.”
The FBI wants companies to know that the Bureau is there for them if they are hacked. But if that hack involves Cryptolocker, Cryptowall, Reveton and other malicious programs that encrypt the contents of a victim’s hard drive, the nation’s top law enforcement agency is warning companies that they may not be able to get their data back without paying a ransom.
“The ransomware is that good,” said Joseph Bonavolonta, the Assistant Special Agent in Charge of the FBI’s CYBER and Counterintelligence Program in its Boston office. “To be honest, we often advise people just to pay the ransom.”
According to According to FBI Cyber Division Assistant Director James Trainor the bureau has since changed its official standpoint and now (2016) they not only try to raise the awareness of the seriousness of the problem and very much are against paying the ransom in order to regain access to encrypted files and systems.
The FBI doesn’t support paying a ransom in response to a ransomware attack. Said Trainor, “Paying a ransom doesn’t guarantee an organization that it will get its data back—we’ve seen cases where organizations never got a decryption key after having paid the ransom. Paying a ransom not only emboldens current cyber criminals to target more organizations, it also offers an incentive for other criminals to get involved in this type of illegal activity. And finally, by paying a ransom, an organization might inadvertently be funding other illicit activity associated with criminals.” If you become target of such a malware attack, it’s recommended to contact your local FBI field office and report the incident to the Bureau’s Internet Crime Complaint Center. Read more on FBI’s website.
What’s our take on the subject?
While the FBI and others may have recommended people just pay the ransom – and it may seem to be the only way under specific circumstance as we’ve seen in media in the recent past – our professional advice is to do otherwise. Complying with ransomware criminals is not much different from buying “hot merchandise” off a “street vendor” as it only opens up the door and encourages future illicit attacks.