Ransomware Prevention: What Can You Do to Protect Yourself

What is it?
We have seen it way too many times and it’s getting worse. It is truly nasty, nasty malware. Back in a day you would get infected, get cleaned up, reinstalled, etc. and wonder often who and why writes and disseminates those viruses? Today, it’s a serious business as the bad guys do it for the $$$. Although it started with indiscriminate campaigns affecting both home users and businesses, realizing the potential for higher profits, cybercriminals are increasingly focusing on the business space. One gets hit with a Cryptolocker or alike, files get encrypted and next things one sees it a banner flashing on the computer, demanding payment in order to decrypt and recover the files. The reason why this type of ransomware is so dangerous is because once cybercriminals get a hold of your files, no security software or system restore can return them to you. Unless you pay the ransom—they’re permanently gone.
How can ransomware be contracted and who’s the most vulnerable?
While lot of people think this type of malware can be primarily contracted by clicking a rouge link in email or opening a zip attachment there are other ways it can infect your systems.
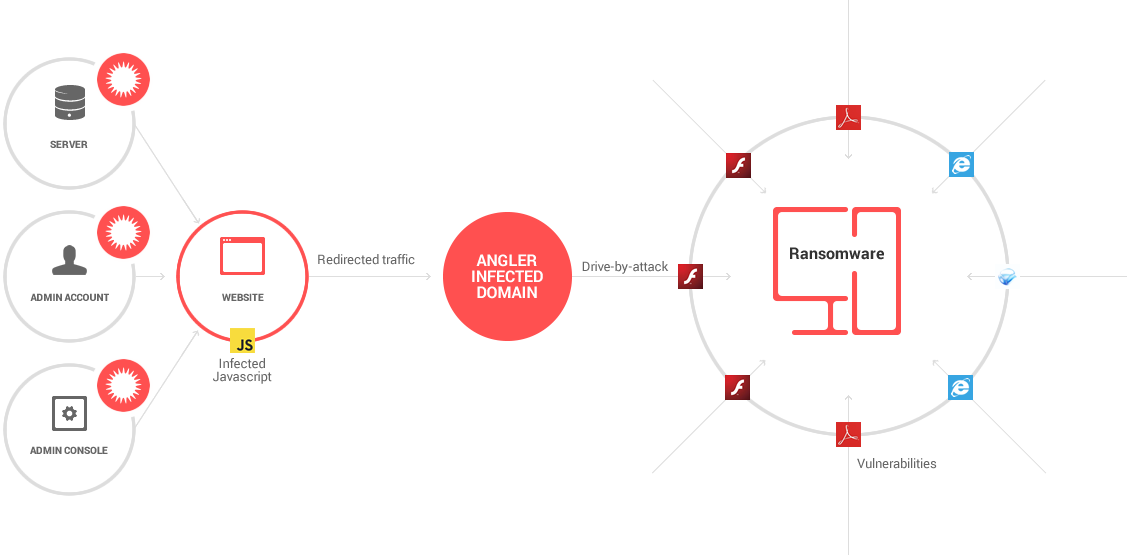
Ransomware gets typically packaged with installation files masquerading as legitimate software updates. They are advertised as updates for Adobe Acrobat, Java and Flash Player. All it takes is a popup prompting you to update Adobe Reader. Once get contract ransomware like infection by not doing anything. Say your browser is out of date or your using older version of Adobe Flash Player or another vulnerable browser plugin a drive-by-attack – even from a legitimate website – can trigger unintentional download of malicious software (malware) onto your system. Game over.
Malvertising. Mainstream news sites, such as The New York Times, the BBC and MSN have fallen victims to a new rash of malicious ads that attempt to surreptitiously install crypto ransomware and other malware on the computers of unsuspecting visitors this year. The aforementioned news sites, entertainment portals were among the victims of a massive malvertising campaign related to the Angler Exploit Kit. This campaign targeted and effectively infected thousands of users in the U.S. The underlying problem is the malicious ads are delivered by a compromised advertising networks have no control over the code quality of the ads that are published on the websites of their customers.
Targeting mobile devices – ransomware threats tailored for mobile platform can be spread through SMS messages, however, they can also make it onto a device by way of untrusted third-party app stores. An example of this is Android.Simplocker or Android.Lockdroid.E, which takes a picture of the victim using the device’s camera and includes the image as part of the very personalized ransom note.
Mac OS X Platform. Though Windows computers are by far the most predominant target of ransomware attacks Mac OS X users are not immune to it anymore. Just in March 2016 In March 2016, a threat known as KeRanger (OSX.Keranger) became the first widespread ransomware to target the Mac operating systems. KeRanger was disseminated via compromised version of the installer for the Transmission Bit Torrent client software.
How to protect yourself against ransomware?
It is imperative to prevent ransomware attacks from happening to you in the first place.
As ransomware techniques and malware are omnipresent and continually evolving – and most anti-malware programs rely on databases of rules and malware definitions to detect it – by the time malware is detected it’s often too late. You should focus on two main aspects in particular:
Take preventive approach in the areas of:
Prevention
- Robust and current technological prevention measures and controls
- Invest in state of the art cybersecurity (if you can afford it)
- Start with an antivirus with active monitoring
- Multilayered protection: anti-malware and anti-ransomware to thwart advanced malware attacks such as ransomware
- Raising personnel of awareness: keep your staff informed as most common ways to get infected with ransomware is through social engineering
- Educate yourself and staff on how to detect phishing campaigns, suspicious websites, and other scams
- Technical training for employees on dos and don’ts online
- Finally, stay informed and exercise common sense. If it seems suspect, it likely is.
Comprehensive Backup
Develop and implement robust business continuity and disaster recovery plan for your organization
- Implement multilayered backup solution
- Intelligent Business Continuity solution
- Have comprehensive data protection
- Reliable hybrid backup system
- Real-time backup and frequently test its effectiveness (restore drills)
- Cloud storage/backup service with high-level encryption and multiple-factor authentication
Yes, the aforementioned bullets sound a bit like corny tautology, but we can’t stress importance of a comprehensive backup system in place to protect your businesses’ data against ransomware.
While data backup is one of the key pillars of combating ransomware infections there have been cases of ransomware encrypting backups. Therefore, you need a comprehensive backup system like Datto that is capable of malware detection via an automated analysis of the backup images.
How serious is it?
Here are a few interesting key points from Symantec’s Ransomware and Businesses 2016 report:
- The Services sector, with 38 percent of organization- al infections, was by far the most affected business sector. Manufacturing, with 17 percent of infections, along with Finance, Insurance and Real Estate, and Public Administration (both on 10 percent) also figured highly.
- The average ransom demand has more than doubled and is now $679, up from $294 at the end of 2015.
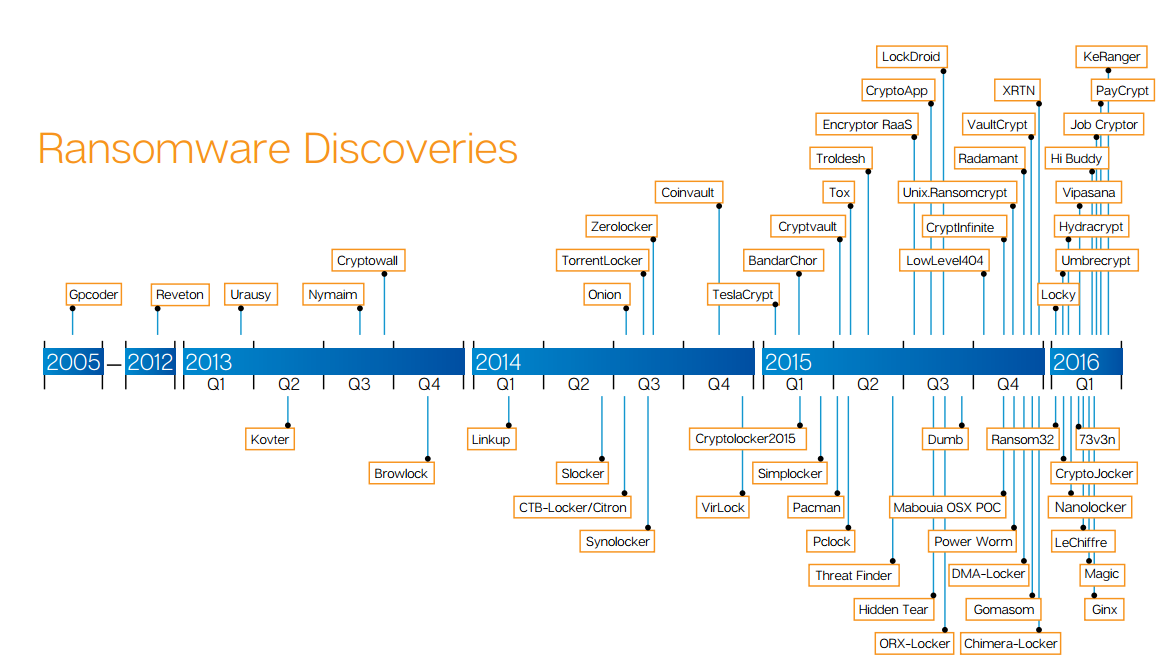
- The number of new ransomware families discovered has been steadily increasing since 2011. Last year was a record high, with 100 new families discovered.
- The advent of ransomware-as-a-service (RaaS) means a larger number of cyber criminals can acquire their own ransomware, including those with relatively low levels of expertise.
- The shift towards crypto-ransomware has continued. All bar one of the new variants discovered so far in 2016 are crypto-ransomware, compared to around 80 percent last year.
- Between January 2015 and April 2016, the US was the region most affected by ransomware, with 28 percent of global infections. Canada, Australia, India, Japan, Italy, the UK, Germany, the Netherlands, and Malaysia round out the top 10. Around 43 percent of ransom-ware victims were employees in organizations.
Source: Symantec Special Report: Ransomware and Businesses 2016
Ransomware Stats and numbers
- It’s been estimated that in 2016 it cost U.S. businesses over 75 billion dollars in downtime!
- 46% of ransomware infections in come via phishing attacks
- Upward 63% of businesses report a malware attack lead up to business-threatening downtime
- Nearly 50% SMBs report critical data loss due to ransomware infection
- According to U.S. Department of Homeland Security the number one solution against ransomware is backup and disaster recovery plan