Phishing Scams and Attacks. How to Prevent CEO Phishing
Spear phishing has been on the rise as cyber criminals have been exploiting it in many ways and on many levels nowadays, especially by utilizing social engineering. It’s been estimated the number of victims of CEO phishing scams has gone up 270% since the beginning of 2015, totaling over $2.3 billion in losses to 17,000+ organizations. Pretty staggering, huh?
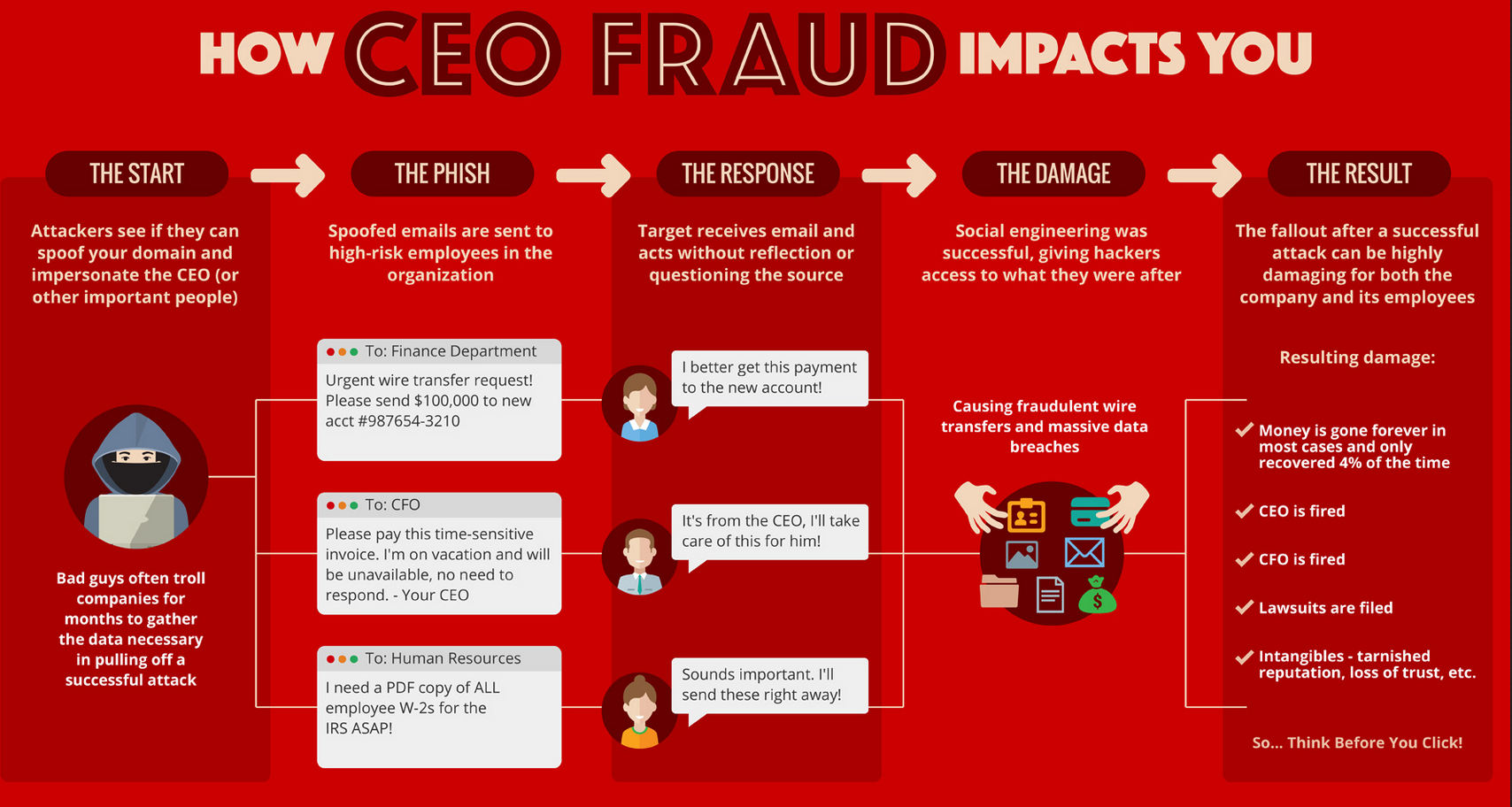
How does CEO phishing work? Unlike regular phishing emails, which are sent out in great numbers to potential victims who have no relationship to each other, CEO spear phishing emails are highly targeted and sent to only a few select victims at a specific organization. E.g., a CFO working at company X gets an urgent email from the president from company X requesting to transfer money or a CEO imposter asks an employee to provide sensitive financial information leading up to eventual monetary losses. Since these requests seem to come from the C-level executives the employees tend to act quickly to please their superiors.
CEO Phishing Detrimental Results
Source: knowbe4.com
A real life example. One of our customers has almost fallen for this phishing trick a few years back. One morning the company’s controller received an email from the company’s CEO requesting to wire 10K to an account. The CEO tends to communicate with staff mostly via email and she’s usually on the go, out of town type of boss, so it seemed OK at first glance. However, the controller called her boss to confirm the legitimacy of the request and – lo and behold – it turned out to be fake.
Then the investigation by the CEO started and IT was first on the grill: “Why did we get this email into our system in the first place? We have spam and content protection system after all?!?!?” Yes, it turned out to be a spoofed email that it should have been intercepted by spam filter, but their definitions were not up to date and it was left through and delivered to user’s mailbox. What’s more interesting and worth noting here is that we discovered then that the company had posted contact info of their key staff (including all VPs) along with their titles, direct phone numbers and individual email addresses on their website! It doesn’t take much to plot such a scam attack. Although it was a good lesson learned for our client, they still chose to keep all the individual contact details on their website…
In some cases, the hackers first phish the targeted CEOs themselves, tricking them into providing their login credentials so that the hackers can send emails directly from their inbox – and possibly use the same credentials to log in to other company systems. In others, hackers send emails from spoofed email accounts with domains that are very similar to the company’s domain. CEO phishers perform research before launching their attack; hackers examine the target company’s website and social media networks and learn about the company’s structure, employees, their positions and responsibilities within the company, even their personal interests and hobbies – anything that they could use to make the phishing email look more genuine.
Again, hackers prey on human vulnerabilities by exploiting human engineering tactics and many big name businesses and organization have fallen victims of CEO phishing.
Here are a few ways to minimize CEO spear phishing
Do not depend on email spam filters to prevent CEO phishing.
While spam filters intercept most regular phishing emails, CEO imposter emails often bypass them because only a few emails are sent at a time, and they do not contain wording that spam filters pick up on (like “porn”). Hackers take time to make them look like legitimate business correspondence.
You can mitigate these vulnerabilities and prevent or curtail these attacks by following these business practices:
Cultivate healthy skepticism.
One of the human vulnerabilities CEO phishers exploit is employee desire to be responsive to superiors – especially the president or CEO. Employees should be encouraged to ask questions about any requests that seem “off,” even if the request appears to have come from the CEO or another top brass executive. Establishing strict and specific authentication protocols helps with this; if employees know what the company’s protocol is, they are better able to recognize requests that do not appear to follow it
Establish and enforce protocols for initiating and carrying out wire transfers, payments and releases of company sensitive Information.
The toy maker’s Mattel loss occurred because wire transfers required only the approval of two high-level managers – of which the targeted finance employee was one, and the CEO was the other. The Federal Trade Commission recommends implementing a payment system that requires a purchase order that is approved by both a manager and a finance officer; a multi-person approval process for transactions exceeding a certain dollar amount coupled with phone verification process for all fund transfer requests and any changes to vendor payment information. Likewise, the release of employee W2 data and other sensitive information should be subject to the approval of multiple parties and a verification process that ensures the party requesting it has the legal right and a legitimate reason to access it. Furthermore, company policy should prohibit highly sensitive information – whether be trade secrets, bank account numbers or employee Social Security Numbers – from being ever sent via email (that is inherently an insecure medium of communication).
Educate you staff to keep their “antennas up” and recognize the telltale signs of phishing emails.
Although CEO phishers go to great lengths to make their emails look legitimate, many attacks originate overseas, with the emails composed by hackers who are not fluent in English or just plain sloppy. As a result, the email may use British spelling, contain punctuation, spelling, or grammar mistakes, or be worded oddly. The salutation or the closing may also be off; an employee of Main Line Health noticed the fraud because the fake email was signed “John Lynch” – and the employee knew that Mr. Lynch went by “Jack.” Employees should also be trained to proofread reply-to addresses and look out for spoofed domains that are only slightly different from the company’s actual domain.
Be cautious and think twice before publishing information on company’s websites or social media channels.
Because CEO phishers comb through company websites and social media networks and seek personal information on executives and employees, information about the company’s activities, such as new clients and new markets, organizations should be careful about what they post publicly on the web. If you don’t have a compelling need to list your officers’ names and email addresses on your websites, then don’t. Analogously, organizations should educate their employees on the dangers of posting too much information on their personal sites, as a hacker looking to launch a CEO phishing attack may examine employees’ personal social media feeds too.
Conduct penetration testing drills.
Organizations that have dedicated internal security staff should conduct regular penetration test drills aimed specifically at social engineering techniques such as phishing. These tests involve sending “phishing” emails to employees and executives to see if they click on them or report them. The results can be used for employee education and, if necessary, for restricting the system access of certain users. If you don’t have security personnel on staff you can enlist the services of a managed security services providers (MSSP).
Deploy endpoint content filtering and protection solutions.
Educating you staff and implementing and enforcing strict policies and procedures is crucial. Hoverer that will never work 100%, therefore organizations need to deploy endpoint protection solutions in coupled with content monitoring and filtering. Modern firewalls utilize cloud based security analysis can also protect users from clicking rogue URLs contained in an email.
Most companies don’t enforce content filtering for remote workers or people utilizing their own equipment when accessing corporate resources. This is another new arena that companies are going to have to figure out how to tackle…ensuring that employees are protected even when they are on their own devices on their own networks.
Because of ever evolving nature of technology and hackers never stop looking for vulnerabilities that can be exploited, an organization’s cyber security efforts are never complete. Many organizations simply don’t have the resources to address all of their cyber security needs internally, which is why partnering with managed security service providers is a smart investment. Cyber security is the core business competency of MSSPs and they can help organizations stay on top of the latest emerging threats, such as CEO phishing, by supplementing an organization’s internal personnel or providing a dedicated on-site security team as warranted by particular circumstances.
