How to Prevent CEO Phishing
Phishing Scams and Attacks. How to Prevent CEO Phishing
Spear phishing has been on the rise as cyber criminals have been exploiting it in many ways and on many levels nowadays, especially by utilizing social engineering. It’s been estimated the number of victims of CEO phishing scams has gone up 270% since the beginning of 2015, totaling over $2.3 billion in losses to 17,000+ organizations. Pretty staggering, huh?
How does CEO phishing work? Unlike regular phishing emails, which are sent out in great numbers to potential victims who have no relationship to each other, CEO spear phishing emails are highly targeted and sent to only a few select victims at a specific organization. E.g., a CFO working at company X gets an urgent email from the president from company X requesting to transfer money or a CEO imposter asks an employee to provide sensitive financial information leading up to eventual monetary losses. Since these requests seem to come from the C-level executives the employees tend to act quickly to please their superiors.
CEO Phishing Detrimental Results
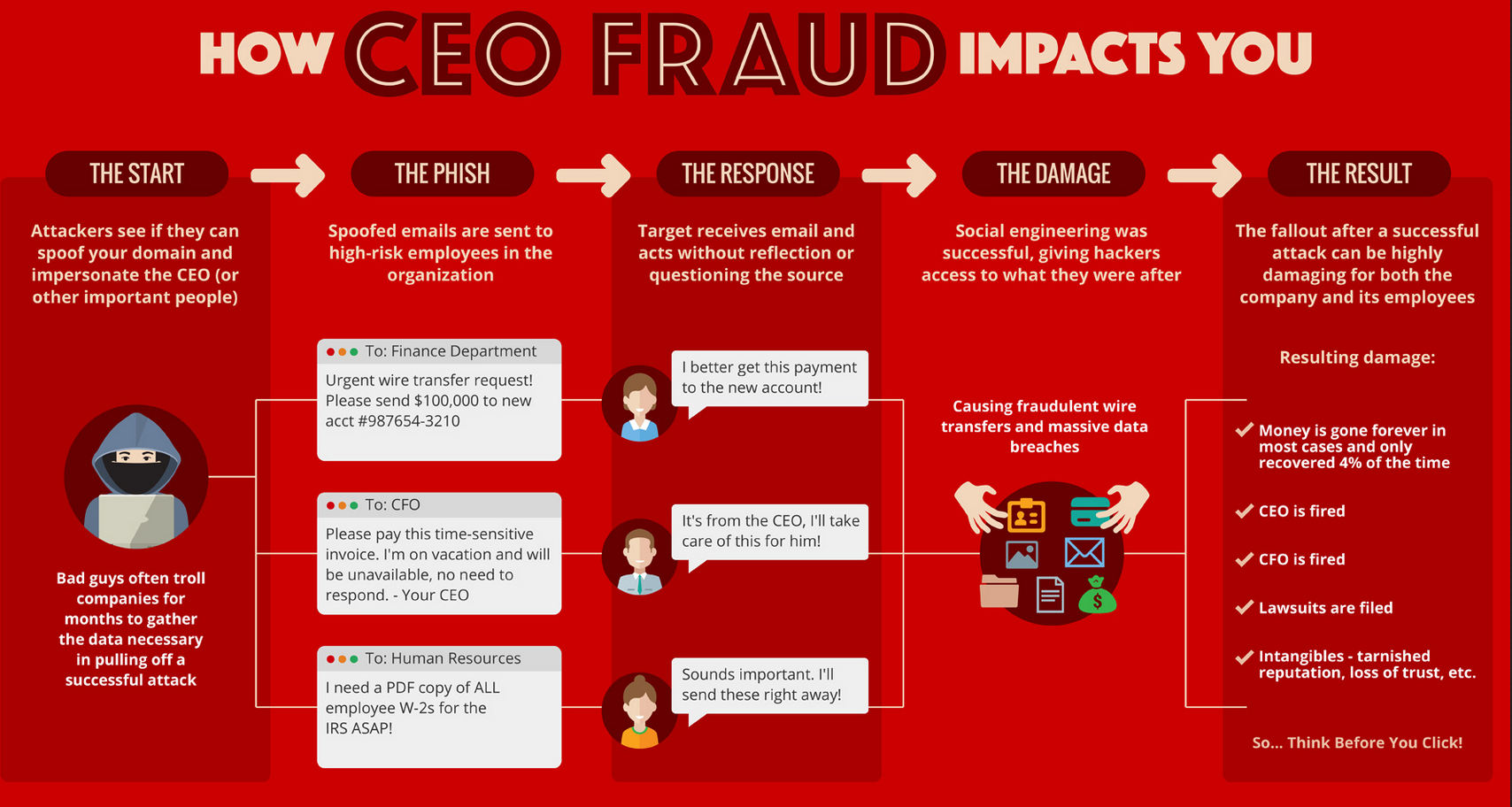
Source: knowbe4.com
A real life example. One of our customers has almost fallen for this phishing trick a few years back. One morning the company’s controller received an email from the company’s CEO requesting to wire 10K to an account. The CEO tends to communicate with staff mostly via email and she’s usually on the go, out of town type of boss, so it seemed OK at first glance. However, the controller called her boss to confirm the legitimacy of the request and – lo and behold – it turned out to be fake.
Then the investigation by the CEO started and IT was first on the grill: “Why did we get this email into our system in the first place? We have spam and content protection system after all?!?!?” Yes, it turned out to be a spoofed email that it should have been intercepted by spam filter, but their definitions were not up to date and it was left through and delivered to user’s mailbox. What’s more interesting and worth noting here is that we discovered then that the company had posted contact info of their key staff (including all VPs) along with their titles, direct phone numbers and individual email addresses on their website! It doesn’t take much to plot such a scam attack. Although it was a good lesson learned for our client, they still chose to keep all the individual contact details on their website…
[…]
