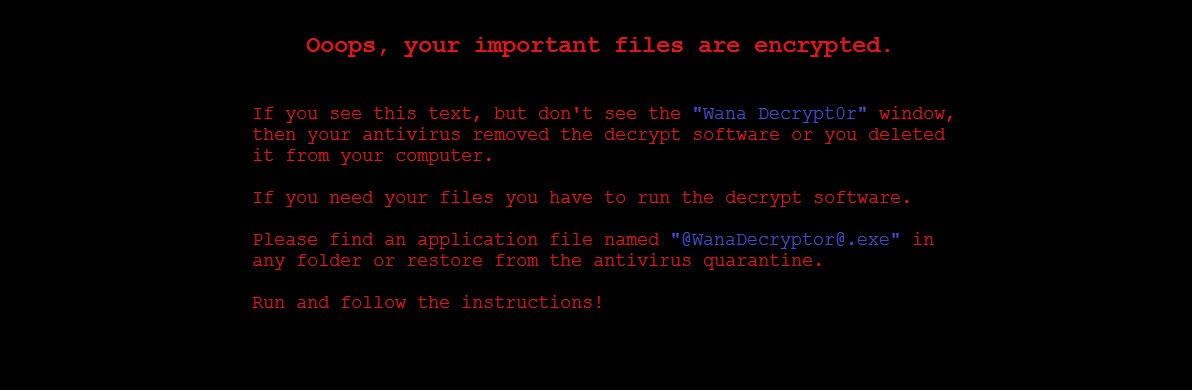
How to prevent WannaCrypt /WannaCry ransomware?
Over the weekend of May 12th 2017, the world experienced one of the most severe ransomware outbreaks in history, with businesses of all sizes in over 150 countries impacted. As ransomware becomes a household name, one thing is for certain: Global cybersecurity has reached a moment of emergency. This is just the beginning of ransomware attacks in 2017.
How can I get infected by WannaCrypt?
According to the security experts at Malwarebytes, unlike the known ransomware variants, WannaCry doesn’t require a victim to open a phising email or visit a web page injected with a malicious code. It goes out and scans the Internet for the windows systems that haven’t been patched for an exploit of Microsoft called EternalBlue. If a vulnerable computer is found, it can contract this nasty malware behind the scenes and its data will get encrypted and permanently gone. You don’t to get into paying ransom to criminals.
How to protect from its detrimental effects?
Keep your Windows operating systems updated
Make sure to install most recent security patched released by Microsoft (the one specifically addressing the said malware has been published on March 2017 – Microsoft Security Bulletin MS17-010.) If automatic updates are enabled or the update has been manually installed, their servers are protected. The supported Windows versions are:
- Windows Vista
- Windows Server 2008
- Windows 7
- Windows Server 2008 R2
- Windows 8.1
- Windows Server 2012
- Windows Server 2012 R2
- Windows 10
- Windows Server 2016
We encourage the installation of the update as soon as possible on any Windows operating system vulnerable to the exploit.
For those unfortunate ones, still with that Windows XP PC hidden in the corner running the Nurse Call system or that Vista box running the video surveillance system Microsoft has released special edition of patches to protect the aforesaid systems. Follow the “Customer Guidance for WannaCrypt attacks” detailed here.
Despite being out of support, Microsoft has taken the extraordinary step to release security patches available here to protect against the said vulnerability for the following operating systems:
- Windows 8 x86
- Windows 8 x64
- Windows XP SP2 x64
- Windows XP SP3 x86
- Windows Server 2003 SP2 x64
- Windows Server 2003 SP2 x86
Disable Server Message Block (SMB) version 1 (SMBv1) on your systems
Since this attack type will likely evolve over time, any additional defense-in-depth strategies will provide additional protections. (For example, to further protect against SMBv1 attacks, you should consider blocking legacy protocols on their networks). Here’s how to disable SMBvs1. Make sure to test your legacy software system if by disabling SMBv1 you don’t cripple their functionality.
Have a current anti-malware software running on all systems
Make sure you have a working and tested backup system for your critical files
Follow the 3-2-1 rule in your backup strategy:
- Have at least three (3) copies of your data
- Keep these backups on two (2) different media sets
- Store one (1) backup offsite
Implement a comprehensive backup solution that will follow 3-2-1 rule by storing them in specified offsite locations and automate your backups.
To recap, the basic questions to ask for your business are:
- Do you have backup and disaster recovery system in place?
- Is all of your software up-to-date?
- Is your antivirus software current?
- Are your Microsoft systems patched?
Let’s get your business ready for what’s to come. Call us today and let us help you deal with protecting your business from calamities such as Ransom:Win32/WannaCrypt