How bad is Bad Rabbit Ransomware?
According to Symantec Corp a new strand of ransomware called Bad Rabbit, which is an updated version of NotPetya, was first reported in Russian and Ukraine this week. It then has found its way into Europe and the United States. It appears to be the third major outbreak of the year and it draws comparisons to this year’s WannaCry and Petya epidemics.
How does Bad Rabbit propagate?
Bad Rabbit targets Windows OS and it thrives on social engineering by masquerading itself as the ole Flash update on compromised websites. The infection chain and component usage is identical to NotPetya ransomware. It carries a database of hard-coded usernames and passwords, most likely to brute force entry into devices on the network. According to SonicWall Capture Labs Threat researchers, Bad Rabbit spreads using the SMB and WebDAV protocols across Windows networks.
Infected binary, named Mimikatz uses a named pipe and retrieves the before deleting itself. It then attempts to connect to other computers in the same network using the current user credentials and from the said database whichever is successful in accessing the admin$ administrative share of the remote computers. It also creates a service on the remote computer, first directly by connecting to the remote service manager and if does not work then using WMIC (Windows Management Instrumentation Command-line).
What’s the damage?
The infected DLL binaries create a scheduled task which reboots the system after 15 minutes and it registers the DiskCryptor driver to load on subsequent boot. Another scheduled task is to run the Encoder/Decoder binary (dispci.exe) on startup. Once windows boots, the dispci.exe connects to the DiskCryptor to perform the rest of the encrypting. What is also encrypted is MBR (Master Boot Record) and the logical volumes of the first hard drive before rebooting the system. On reboot the infected MBR presents a password prompt.
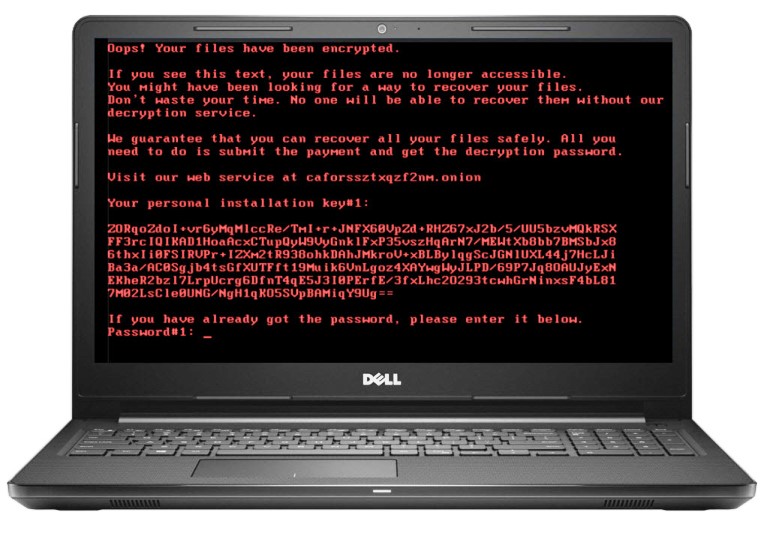
That basically means your computer and/or server just got bricked!!! Ouch.
Can I get my computer unlocked and data decrypted?
Unlike the previous NotPetya version, this version has capability to completely reverse the encryption and give the files back. The ransomware demands a payment of 0.05 bitcoin ($275) but you’re never sure whether paying the ransom unlocks your computer’s files. And the timer is set to 40 hours to pay!
How weak / strong are your user’s passwords?
Recent Verizon’s data breach report showed that 81% of hacking-related breaches used either stolen and/or weak passwords. Humans tend to be the weakest link in your network security, using weak passwords and falling for phishing and social engineering attacks.
How Can I Protect my network against Bad Rabbit ransomware?
Follow general security best practices, especially:
- Keep operating systems security patches current
- Keep endpoints with current malware definitions and security subscriptions to stop threat at gateway
- Keep firewall and end point firmware up to date
- Have multiple layers of data backups as well as proven business continuity solution
- Implement a network sandbox solution to discover and mitigate new threats
- Promote and enforce good passwords hygiene
- Educate: propagate security awareness among your staff
- Rinse and repeat
