Heads up – Cyber Extortion Threats
There’s a new aggressive form of email attacks that you need to warn your coworkers ,employees, friends and family about. The cyber criminals have beta tested and refined it in Australia, and now the first incidents have been trickling into the States.
Cyber thugs are taking advantage of the vulnerability of intellectual property, threatening to release potentially embarrassing and detrimental information to the public and encrypting data to render it useless to the its owners, among other sinister practices.
The sophisticated attackers are targeting potential victims in an email sequence that starts with pornography and adult dating links, which are then followed up with extortion attempts.
Unlike the risks associated with more traditional cybertheft, such as the loss of customer account data, the risks and costs related to extortion can be indirect and difficult to assess. The conventional thief looks for information, such as credit card numbers, that can be easily converted to money. This data has a direct market value — at least on the black market.
The cyber extortionist, however, takes advantage of information that is valuable to its rightful owner by rendering the data unusable and holding it for ransom or threatening to release it publicly.
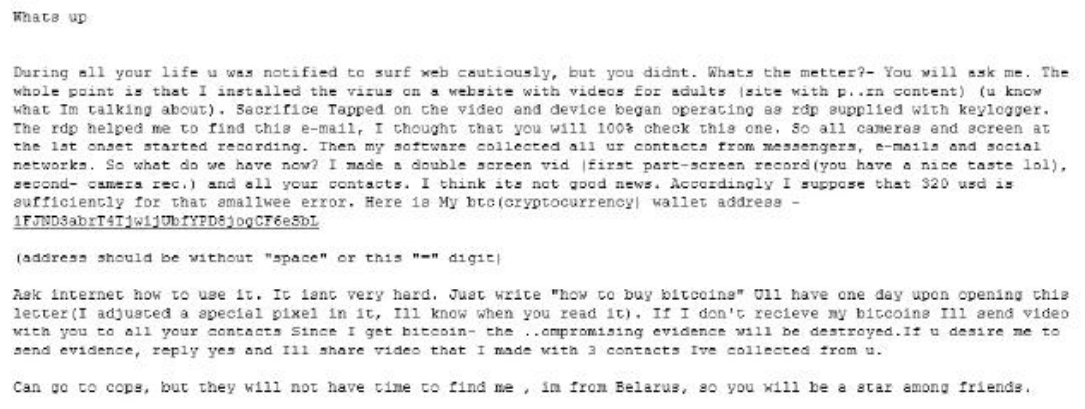
According to IT security company Forcepoint, the latest scam threatens to steal users’ privacy, emails that say, “look at this”, then “we know what you just looked at” and demand $300+ payment in Bitcoin.
The email claims that a virus was installed on a porn website which recorded the victim through their webcam. “Then my software collected all your contacts from messengers, e-mails and social networks,” it says. “If I don’t receive my Bitcoins I’ll send video with you to all your contacts.”
Although these are similar to webcam blackmail – where a cyber attacker inconspicuously records record a video of the computer user, often with clothes off, threatening to publish the video public unless ransom is paid – they are fake in most cases.
Carl Leonard, principal security analyst at Forcepoint, said cyber-extortion was a prevalent tactic today. While it largely takes the form of ransomware, he said data exposure threats were growing in popularity.
Company Email Addresses Specifically Targeted
Leonard said company email addresses were specifically targeted, which would have added additional pressure to potential victims “since it implies that a recipient’s work PC was infected and may therefore taint one’s professional image”. “It is important for users to verify claims from the internet before acting on them,” he said. “Most online attacks today require a user’s mistake before actually becoming a threat. This is something that can be mitigated by addressing the weakness of the human point.” We concur.
But Leonard said the scale of this campaign suggested the scammers were bluffing about having compromising information. “If the actors did indeed possess personal details of the recipients, it seems likely they would have included elements [such as name, address or date of birth] in more targeted threat emails in order to increase their credibility.
How to protect from Cyber Extortion Attacks?
Protective encryption of data can safeguard against it being exposed by cyber-criminals. However, this does not protect against further unauthorized encryption that can and will render the data inaccessible. Frequent and prompt backup of generated data can protect the data from tampering, such as covert encryption, but does not keep attackers from releasing data taken from stolen originals.
Protecting against these types of attacks relies on utilizing a defense-in-depth strategy.
- Perform regular vulnerability scans on all your outward-facing networks and make it part of your company’s security policy.
- Utilize intrusion prevention systems at application layer such as firewalls to provide protection against web-based attacks.
- Run network penetration tests that will help you identify network vulnerabilities before criminals do.
Feel free to disseminate among your staff, coworkers and friends. Be safe out there.
